Email Traffic Reports
The Analyze Email Traffic pages provide a list of common questions to provide you with helpful views into your email ecosystem. Each view is a detailed report about your email ecosystem and shows you both a graphical representation and a list of the information in each report.
When viewing the reports, you can:
- Hover over the sections of the graphical representation to see pop-up capsule summaries of the specific data presented.
- Click on a section of the graphical representation to filter by that subset of data.
- Click on any link in the list to filter by that subset of data.
- Share an Email Traffic Report
- Schedule an Email Traffic Report
Available Reports
DMARC Protection provides a variety of reports for your outbound email traffic.
The following table indicates the reports available for you to view. Reports are categorized into three types.
| Report Name | Inbound |
|---|---|
| The Big Picture | |
| What does my DMARC trend look like? | 
|
| What's happening to messages failing DMARC? | 
|
| What messages pass DMARC with SPF & DKIM? | 
|
| Which ISPs do I send email to? | |
| How much email using my domains is legitimate? | 
|
| Things I Can Fix | |
| What are my SPF problems? | 
|
| What are my DKIM problems? | 
|
| Are any legitimate messages being rejected? | 
|
| What legitimate subdomains don't I know about? | 
|
| Who is Spoofing Me? | |
| How much spoofed email am I blocking? | 
|
| What subdomains are being used to spoof me? | 
|
The Analyze > Email Traffic page includes a toggle that switches from reports on outbound email traffic to reports on inbound email traffic. (Outbound is the default view.)
You can adjust the filter options for every report to help you get to the information you need. You can:
- Filter each report for a single domain or domain group.
- Increase or decrease the data range from the default value of 2 weeks. It is recommended to increase the date range, for example to 90 days, to see trends and patterns in your sending. (For example, 2 weeks is too short of a time span to see data from a newsletter sent quarterly.)
- Change the granularity of message grouping (daily, weekly, or monthly)
- Modify the Message Origin of certain reports; for example, in some views, it may make sense to include or exclude certain categories of messages.
See Configure Email Traffic Reports for more details on how you can customize email traffic report views.
When you're just getting started monitoring your email traffic in DMARC Protection, you could get useful information by reviewing the following reports first:
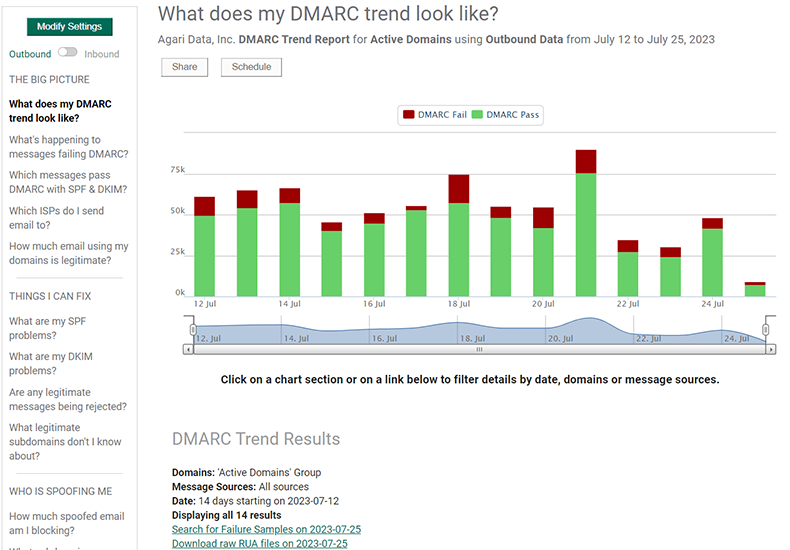
What Does My DMARC Trend Look Like?
This report shows the general trend for DMARC pass and fail for messages. As you increase authentication from all of your Senders for all of your domains, you can determine when you have a sufficient amount of email is passing DMARC checks so that you can move to a Reject policy with confidence.
A great place to start monitoring data is with the default view: the What’s My DMARC Trend Look Like? report.
At this point, you may only have a few domains generating data into DMARC Protection, and those domains may have no authentication whatsoever.
Drill into specific data by clicking any of the links in the DMARC Pass or DMARC Fail columns.
Clicking the link for a specific domain in this view yields a report or all IP addresses sending on behalf of that specific domain in the selected time-frame.
You can drill down even further by clicking the DMARC Pass link for any IP address listed in this table.
What's happening to messages failing DMARC?
Message which fail DMARC checks can have different actions taken on them, depending on a) your policy and b) the actions of the receiver. Use this view to examine failing messages and see how various large receivers (Google, Yahoo, AOL, Microsoft, etc.) are processing them. Drill into details to examine failing messages on a domain-by-domain basis.
Which messages pass DMARC with SPF & DKIM?
Conversely, this view shows you the passing messages — passing DMARC, passing SPF, or passing both — on a domain-by-domain basis. You can use this view to drill into details and see how each domain doing with respect to authentication checks.
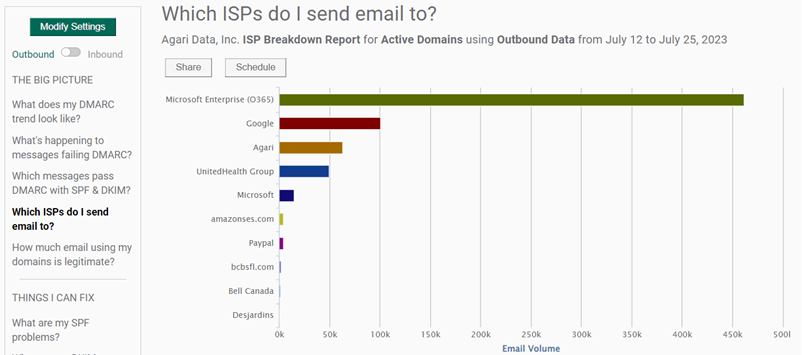
Which ISPs do I send email to?
This report shows all messages reported by a given ISP, broken down by authentication results.
How much email using my domains is legitimate?
In yet another pivoted view, you can the see the legitimate and threat messages, in aggregate volume and on a domain-by-domain basis.
Legitimate messages include any messages which originated from IP addresses within your Sender Inventory (i.e. your approved Senders list), whether they passed or failed DMARC authentication. Also included are messages from outside of your Sender Inventory which passed DMARC authentication, such as auto-forwarded messages which preserve the original DKIM signature.
Threat Messages are those which failed DMARC Authentication and originated from outside of your IP space.
What are my SPF problems?, What are my DKIM problems?
As discussed in Identify SPF Problems and Identify DKIM Problems, you can use these reports to drill into details about SPF and DKIM authentication progress and problems for any domain.
Are any legitimate messages being rejected?
Use this report to determine if any false positives are being rejected at receivers due to your DMARC policy.
What Legitimate Subdomains Don’t I Know About?
Use this report to discover subdomains being used to send messages for your organization.
This is another useful view in the initial stages of monitoring.
The results of this view may shed light on subdomains of your primary domain that may be being used to send email.
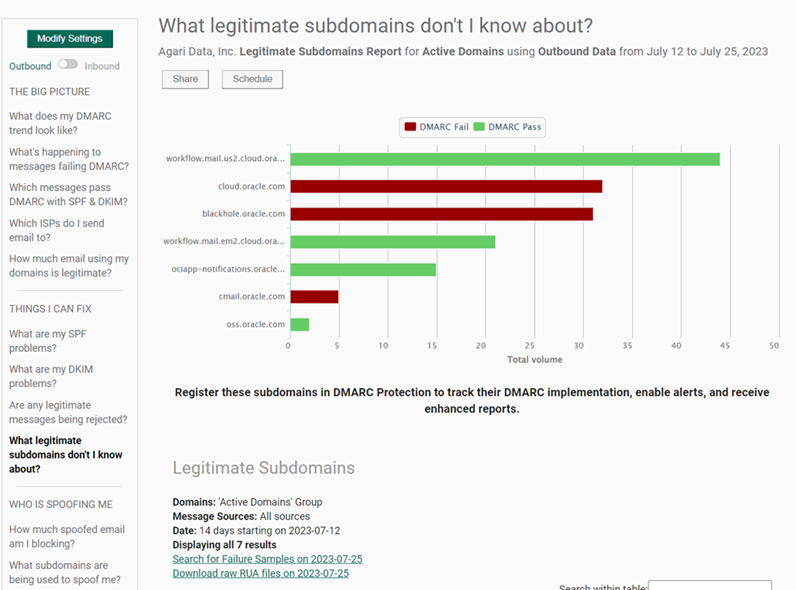
NOTE: Legitimate subdomains in this report are only reported for approved domains.
How much spoofed email am I blocking?
As you implement a reject policy, you can see the benefit of your enforcement policies in this report view.
What subdomains are being used to spoof me?
Like the subdomain report above, you can use this view to discover subdomains are not currently authorized by you to send email. Register the subdomains as defensive domains in DMARC Protection to work towards a DMARC reject policy.
See Also