Organization Settings
Organization settings determine how Cloud Email Protection works in your organization. You manage your organization on the Edit Organization page. The Edit Organization page contains tabs on which settings are collected, and each tab contains sections of related settings. Here, you configure the following categories of settings:
- Administrative Tab
- Administrative
- Organization
- Report
- Sensor
- Enforcement
- Continuous Detection and Response
- User Account
- Affiliate Adminstration
- Microsoft API Permissions Tab
- Message Components Tab
- Processing Exceptions Tab
- Audit Tab
To view or edit organization settings, go to Manage > Organizations, and then click the organization name.
NOTE: You can make changes to the organization settings only if you have the Organization Administrator role. (Certain settings require higher-level roles that are available only to Cloud Email Protection administrators. If you do not see a setting in your view or you cannot change a setting, this is likely the reason.)
Administrative Tab
| Setting | Description |
|---|---|
| Administrative | |
| Organization Name | The name of your organization. This is what you see wherever there is information displayed about or relating to your organization, such as audit trails. You can change the organization name. |
| Symbolic Name | A unique string created from the initial organization name to uniquely define the organization. This identifier is used by the system and is viewable only here. It cannot be changed. |
| Subdomain | The part of the application URL that is unique to your organization. It is a subdomain of ep.agari.com. |
| Creation Date | Shows the date and time that the organization was created. Click |
| Organization Settings | |
| Primary Administrative Contact | The organization user selected here will be the person who will receive all administrative contact from Fortra Cloud Email Protection. |
| Parent Organization | The Partner organization that manages the selected child organization. |
| Organization Type |
Defines if the organization is:
|
| Expiration | Defines when an organization's subscription expires and is up for renewal. |
| Classification Settings | |
|
An organization's classification settings are used for reporting, especially for comparing an organization's aggregate data to industry peer aggregate data. See Reports for more information. |
|
| Region | This is used to determine geographic peers. |
| Industry | This is used to determine industry peers. If your organization isn't categorized by one of the defined choices, select Other. |
| Mailboxes | This is used to determine peers based on mailbox size range as a proxy for organization size. |
| Exact mailbox count | Enter the actual number of mailboxes in your organization. This should be a number in the range you selected above. |
| Messages Settings | |
|
An organization's message settings determine what messages Cloud Email Protection will ingest. These settings are only available if the Messaging Platform setting in the Sensor Settings section is Microsoft Office 365 or Exchange Online (journaled) or Microsoft Exchange Server (journaled). You will also need to have journaling configured correctly, as explained in Configure Dual Delivery: Office 365 and Configure Dual Delivery: Microsoft Exchange. |
|
| Evaluate Messages |
Defines what messages are ingested. Select from:
|
| Accepted Domains |
Defines the domains for which you accept messages. Required if you select All messages in Evaluate Messages. This should be a list of your domains, including subdomains, that receive your email messages. For example, mycompany.com is your domain, but you have mail.mycompany.com as your email server. These, (and possibly others) should be in this list. Cloud Email Protection uses this list to help determine message directionality. Domains you add to this list will automatically be tagged as internal (if they do not already have a tag). Domains tagged as internal before enabling IIP are also automatically added to this list. If a domain is tagged as internal after IIP is enabled, it is not automatically added to the Accepted Domains list. For more information see Domain Tags |
| Report Settings | |
|
For each attack type, you can select:
Messages with a Trust Score of between 0.0 and 1.0 (on a scale of 0.0 to 10.0) are considered untrusted. Messages with a Trust Score greater than 1.0 and up to 5.0 are considered suspicious. This setting allows you to define whether you want reports for each attack type The default for all attack types except Domain Spoof is Untrusted and Suspicious. |
|
| Continuous Detection and Response Settings | |
|
The Continuous Detection and Response (CDR) Settings section controls how CDR operates in your organization. See Continuous Detection and Response for more information. |
|
| Default enforcement |
Determines the default action for messages determined to be a threat by the CDR threat feeds. For each available threat feed, select:
TIP: Because CDR threat feed rules that affect how messages are identified for enforcement are created for a scope of messages much larger than your organization's message stream and because a Delete action is irreversible, you may want to choose Monitor or Move initially to evaluate how each CDR source affects messages specifically in your organization. |
| Notify |
A list of one or more email addresses. A message will be sent to the addresses in this list when a CDR event matches any messages. TIP:
For a large organization, CDR could generate many messages. Consider creating:
|
| Sensor Settings | |
|
The Sensor Settings section refers to global sensor settings for the organization. |
|
| Operational Mode | Defines how the sensor is placed in the email infrastructure. See Configuring Delivery to the Sensor for more information. |
| Messaging Platform |
Defines the messaging platform. Select:
|
| Original-To Header Name |
Used only for Sensor processing overrides. Leave as-is unless instructed otherwise by Fortra Cloud Email Protection. When a value is entered in this field, the value replaces the Original-To Header when the message is processed by the Sensor. This can help you identify Sensor-processed messages when you are creating policies. |
| Original-Mail-From Header Name | Used only for Sensor processing overrides. Leave as-is unless instructed otherwise by Fortra Cloud Email Protection. |
| Internal MTA IPs |
List IP addresses for any upstream MTA sending traffic that you want to capture. The form accepts CIDR notation for specifying ranges of IP addresses. NOTE: Use this only in the case of upstream MTAs. |
| Allowed Forwarding IPs |
Determines the IP addresses from which Sensors will accept forwarded messages. One or more IP addresses entered in this field will prevent mail forwarding from any IP address not listed. TIP: This is generally used for heightened security measures, and is typically left blank. This also affects the testing of SMTP connections. To add an IP address to the list, enter an IP address into the IP Address field, and then click Add. The IP addresses in this list should be only the IP addresses of the servers in your email infrastructure that forward messages to Sensors. |
| Enforcement Settings | |
| Enforcement allows you to create policies that move messages to a designated folder in the end-user's inbox. Enforcement is available for Gmail, Office 365, and Exchange Web Services (EWS) environments only. | |
| Enforcement | When set to Enable, allows policies to enforce rules on messages based on policy settings. |
| Enforcement Label(s) |
The default enforcement folder can be changed and additional folders set in the Enforcement Settings. These folders are displayed in the Enforce Actions for all Policies in Create / Edit Policy and are the names of the folders or labels that end users will see in their mail client. |
| User Account Settings | |
| Single Sign-On | Determines whether your users need to enter a password in addition to their user name to access Cloud Email Protection or whether they can use your existing authentication. See Single Sign-On (SSO) and Enable Single Sign-On for Your Organization for more information. |
| Session Inactivity Logoff | Determines how long users can stay signed in to Cloud Email Protection before they get signed out automatically. The default is 12 hours. |
| Session Absolute Logoff |
Determines how automatic log off happens. Select from:
|
| Password expiration | Determines the time period before users have to select a new password. The default is Never. |
| Maximum failed login attempts | Determines how many times a user can attempt logins without success before being locked out and requiring a new activation link to be sent. Select Disabled if you do not want to limit login attempts. |
| Password policy |
When you require a password for login (non-SSO), determines the minimum complexity of the password. The default is
Select Custom to modify any of these password characteristics for your users. |
| Affiliate Administrator Settings | |
| Ingest | Enables the ability for the CEP data pipeline to ingest the organizations message data. NOTE: This depends on Graph Ingest or Journaling you set up. |
| Parsing | Set to valid after initial set up. Before setting parsing to valid status, confirm in the CEP web application that properly formatted message data is being ingested. This ensures that only valid data is fed into scoring models. |
Microsoft API Permission Tab
Steps to Disable Enforcement
You must login as a Master Administrator in Fortra Cloud Email Protection in order to disable Enforcement permissions.
-
Go to Manage > Organizations, and then click the organization name.
-
Select Microsoft API Permissions tab.
-
In the Enforcement option, Click Disable. In the Disabling Enforcement pop-up type DISABLE and then click Confirm. The Enforcement account will be permanently disabled from organization.
-
In the Enforcement option, Click Disable. In the Disabling Enforcement pop-up type DISABLE and then click Confirm. The Enforcement account will be permanently disabled from organization.
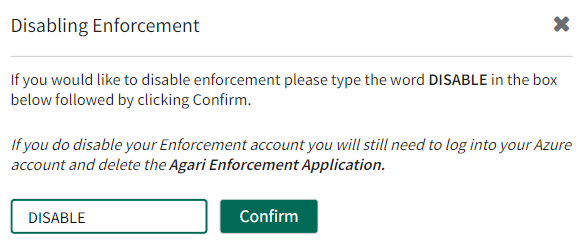
TIP: You will need to login as Global Admin in Microsoft Azure to delete the Fortra Cloud Email Protection Enforcement Application after disabling the same from CEP.
NOTE: To enable Ingest or Enforcement again in your organization, you will have to create a new Enforcement account.
Message Components Tab
Processing Exceptions Tab
| Setting | Description |
|---|---|
| Processing Exceptions | |
|
Processing exception settings are rules that tell Cloud Email Protection which messages it should not evaluate process. Messages that meet ay of these rules will not be evaluated by the Sensor, scored for threats, or managed by policies. Messages not processed by Cloud Email Protection do not appear, individually or cumulatively, in reports or searches. |
|
| Office 365 Spam Processing |
For Office 365 organizations only. When a message is sent through Office 365 spam filtering, it is assigned a spam score, which is mapped to a spam confidence level (SCL) rating. Spam scores of 5 and above are considered spam by Office 365 and are moved by default to users' Junk folders. (Source: Spam confidence levels.) Some organizations have configured a different spam score on Office 365 for which messages are sent to users' Junk folder. Because you generally do not want Cloud Email Protection to process messages that Office 365 has already determined to be spam, the optimal value for this setting is the same as the organization's Office 365 value. |
| Message Scoring Exception Rules |
Defines message rules, rules that tell Cloud Email Protection for which messages to skip any processing. These rules act similarly to message-handling rules in email clients. You select the rule type and enter a value for that type. Available rules are for headers found in messages, headers that include:
To add an exception rule, select a rule type, enter a single value, click Add Exception, and then click Save. The value field accepts only one value (or in the case of X-Header, an X-Header itself and optionally an X-Header value), and does not support wild cards or regular expressions. It is a strict exact text match only (except for Subject, where any subject must contain the entered value anywhere in the message subject to match), and validates for correct values before you can add the exception rule. To delete an exception rule, click the |
Audit Tab
View all historic session activity and data changes for all users of your organization. See Audit Trail for descriptions of each icon.