About Agari Phishing Response
Agari Phishing Response makes it easy for you to effectively and efficiently triage, analyze, and remediate various types of attack messages that are sent to the people in your mail organization or domain. Phishing Response leverages Agari's Identity Graph™ technology, which is a key component of the Agari Secure Email Cloud™ and Agari's suite of email security products.
The Problem
According to industry data, the average cost of an email breach is $7.9 million. The average probability of a breach annually is 14%, so for any company the potential annualized cost is $1.1 million.
96% of email breaches are initialed by phishing. When a breach is successful, the average exfiltration of data is within hours. Yet the average discovery time of email breaches is measured in months.
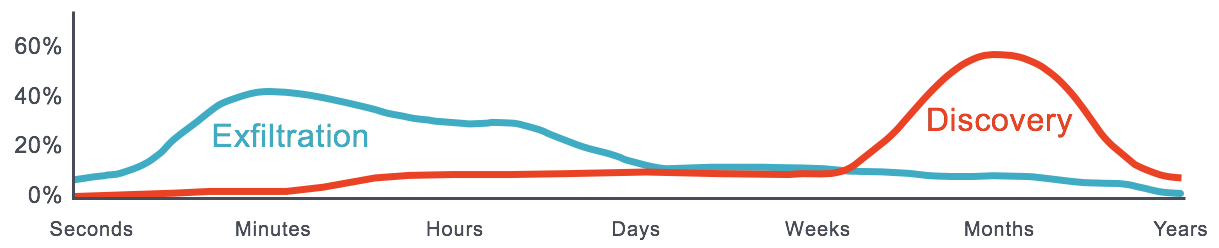
Meanwhile, as education about phishing and other malicious tactics that target company email improves, more employees are identifying and reporting phishing messages.
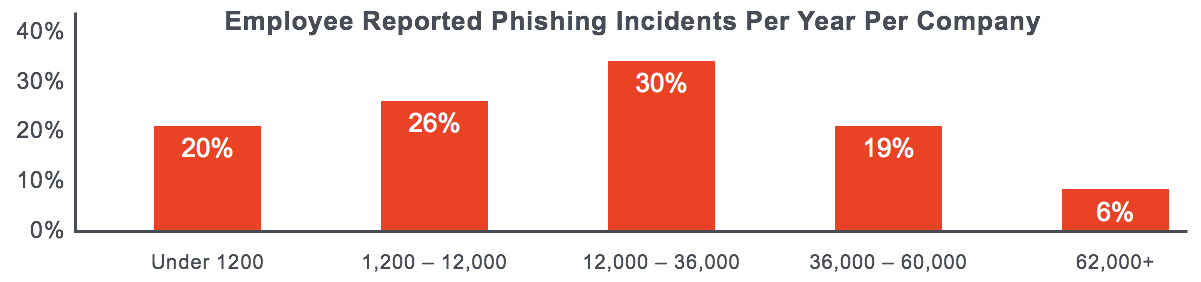
SOC analysts can face tens of thousands of phishing reports annually that, when analyzed using typically available tools, take an average of 5.9 hours per true phish. But the education that increases awareness can be a double-edged sword because up to 50% of phishing reports are now false positives, so an increasing amount of SOC analyst time is taken by dismissing those false positives, instead of investigating and remediating actual threats.
The Solution
Phishing Response captures reports from your employees of phish and other malicious email messages and automates the initial triage and campaign analysis, allowing you to quickly determine if the investigation is an incident.
Phishing Response organizes related messages into investigations, which you then further triage and analyze. If through triage and analysis you conclude that the investigation is an incident, you can then remediate the incident directly within Phishing Response. You can also view reports about Phishing Response activity.
Triage
Triaging reports of phishing and other malicious attacks, where you have to decide what reports are important and indicate attacks, what reports aren't really attacks, and everything in between, has been one of the most tedious and time-consuming aspects of identifying, classifying, and prioritizing those reports. Agari Phishing Response, using Agari's Identity Graph technology, analyzes, classifies, and categorizes employee reports of phishing attacks, auto-classifies those reports, and presents you with the specific information about those attacks in a useful investigation format so you can make informed remediation decisions quickly, reliably, and confidently. The automatic triaging that Phishing Response performs includes analysis to see if an employee report of a malicious attack is a part of a larger attack or campaign.
During your triage, if you discover that the attack is real and it affects your organization, it becomes an incident that you then prioritize, analyze, and remediate.
When you triage investigations in Agari Phishing Response, you can:
- Filter the investigation list view by facets you define
- Search for investigations by a robust set of criteria and message characteristics
- Track time spent triaging investigations
- Classify and prioritize investigations
The information about messages that Agari's Identity Graph can surface to you in Phishing Response allows you to quickly categorize investigations as:
- Malicious, identifying them as incidents
- Spam or benign, and quickly closing them
You can also assign a priority (critical, high, medium or low) to the incidents so you can organize your analysis work.
Analysis
Analyzing reports of malicious messages, where you review message details, including attachments, URLs, and message headers, is how you get a deeper understanding of the nature of the attack. Phishing Response makes all this information easily accessible and easily understandable. The information that the Agari Identity Graph extracts from messages includes:
- Domains, which allows Agari to determine domain reputation.
- IP addresses, which allows insights into the entire IP chain of the message.
- Attachments, which provides integrated information aggregated by VirusTotal and the capability to send attachments to a best-of-breed sandboxing solution (Hybrid Analysis by Crowdstrike) for isolated detonation and analysis.
- URL analysis, which follows down the path of addresses, including redirects, to determine maliciousness. This includes integrated information aggregated by VirusTotal with the capability to send to a sandboxing solution for deeper analysis, and displaying the URLs defanged and an image of the URL landing page provided by RiskIQ.
Remediation
Once you have triaged and analyzed incident reports, Agari Phishing Response provides tools to help you remediate any identified issues and generate reports on your actions.
Phishing Response supports moving or deleting messages from your employees' Inboxes, so once you verify a threat, you can eliminate it throughout your organization.
Reports
Phishing Response provides reporting via an executive dashboard. The dashboard contains the following reports:
- Malicious Investigations Summary
- Impact and Risk Reduction
- Closed Investigations
- Top Targets and False Reports
See Reports for more information.